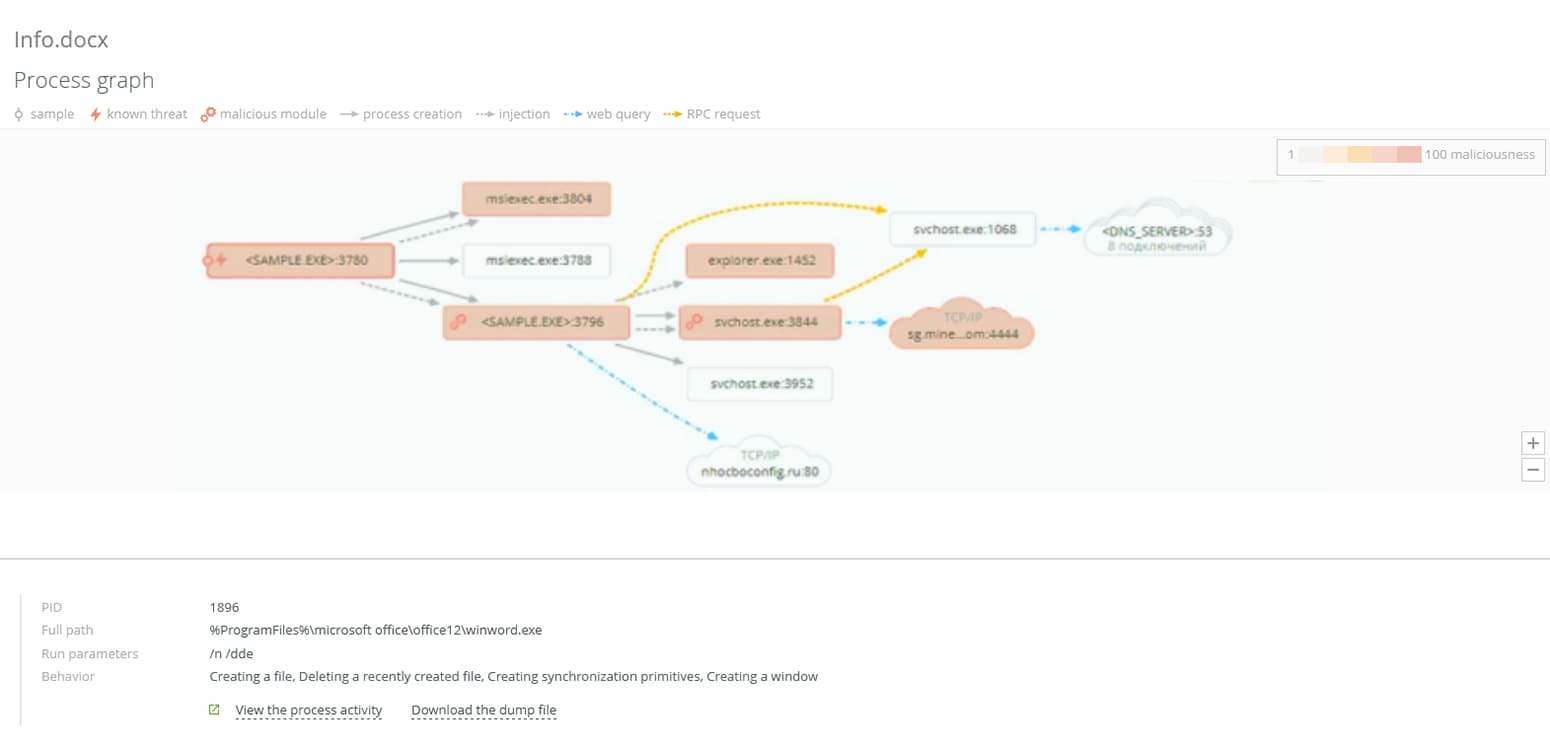
Dr.Web vxCube
Intelligent and interactive analyses of suspicious objects (sandbox)
- Choose between the cloud-based and on-premise versions
- Integrate it into an existing infrastructure
- Set up an environment where objects can be analysed
- Custom Dr.Web CureIt! builds for neutralising specific threats
- For security researchers and cybercrime investigators
Malware analysis by Doctor Web security researchers
No automated routine can ever replace the experience and knowledge of a security researcher. If Dr.Web vxCube returns a “safe” verdict on your analysed file, but you still have your doubts about this result, Doctor Web's security researchers, who have a wealth of experience analysing malware, are ready to assist you.
Anti-virus research requestWith this service, a malicious file of any complexity can be analysed. The resulting report includes:
Information about the malware’s basic principles of operation and that of its modules;
An object assessment: downright malicious, potentially dangerous (suspicious), etc.;
An analysis of the malware's networking features and the location of its command-and-control servers
The impact on the infected system and recommendations on how the threat can be neutralised.